OTP + KBA Authentication
In this use case, issuers can meet the Strong Consumer Authentication (SCA) requirements in PSD2 without needing 100% of their cardholders to be enrolled in a mobile banking application that requires biometric authentication. Since most issuers collect contact credentials and Knowledge-based Answers (KBA) during the cardholder application process, this information is readily available to use across your entire cardholder base.
One-time Passcode (OTP) and Knowledge-based Authentication (KBA) can be used together to authenticate a cardholder during an online transaction. Support for OTP + KBA flows meet both the Possession (OTP) and Knowledge (KBA) requirements that help issuers meet the needs of the PSD2 regulation for Strong Customer Authentication (SCA).
This flow can be supported as a fall back to a primary SCA method such as Biometric, or it can also be used as a primary authentication method if the issuer is not configured for an advanced authentication method such as OOB or Biometric. For a successful authentication, both factors (OTP and KBA) must be successfully validated by the cardholder. If the cardholder fails to validate both factors successfully, the authentication request will fail, and the cardholder will not be informed about which one of the two factors failed.
| Pros | Cons | RDX Calls |
|---|---|---|
| Reach more cardholders with information already on file | Two-step authentication process | Stepup |
| Meet SCA requirements for SCA2 | Cardholders may forget their KBA | Initiate Action |
| Use as fallback method if biometrics is unavailable | Validate |
OTP + KBA Flow Diagram
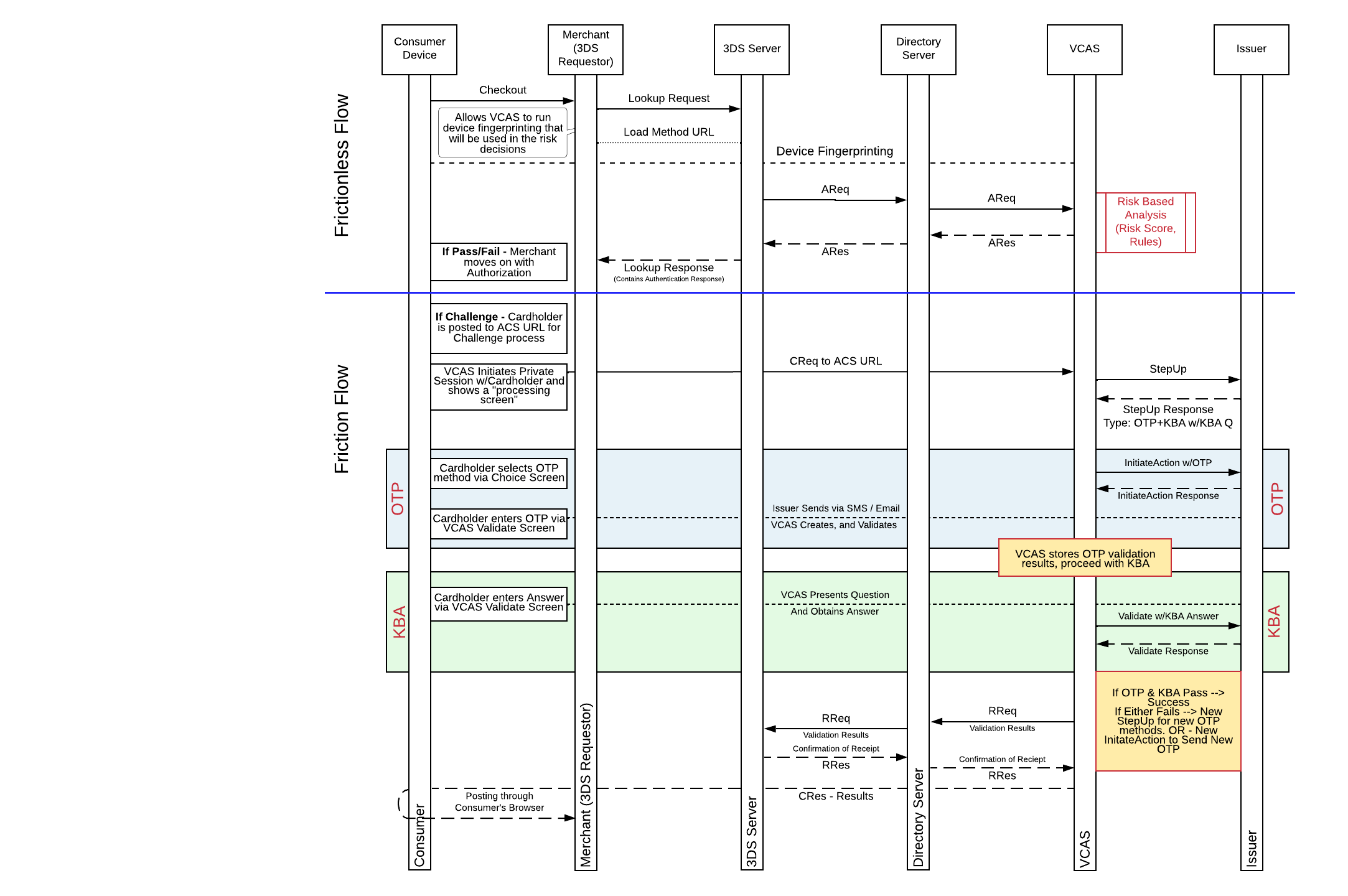
Required RDX Calls:
Updated about 1 month ago